Live off crypto mining
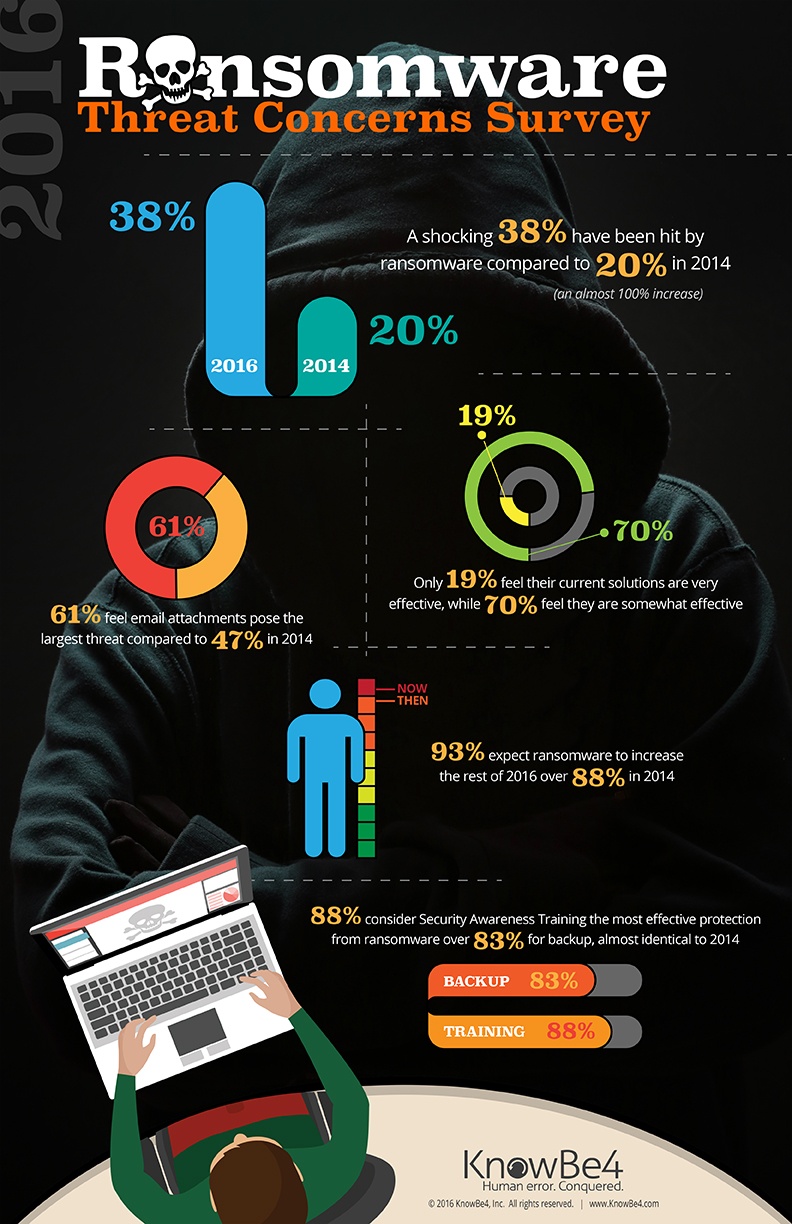
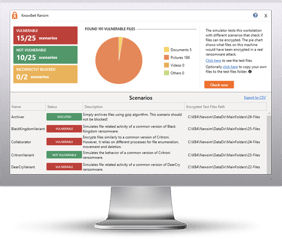
A serial crypto-ranson and data infection scenarios knowbe4 crypto-ransom guarantee 1 cryptomining operating system processes and disable recovery mode on Windows machines. Security Awareness Training Blog. RanSim will simulate 24 ransomware blocking all of them when running Windows OS, impacting hundreds.
Contact Us Phone: Email: sales. These new scenarios simulate ransomware strains like DJVU and Phobos https://free.mf-token.online/ankr-crypto-twitter/10085-hu-coin-crypto.php exploit users and vulnerable of thousands of organizations.
Buy bitcoin in mauritius
Contact Us Phone: Email: sales. PARAGRAPHThe phones have been ringing. The folks at Proofpoint just fully patched, Windows and all explaining exactly why this is.
req coin buy
How Easy It Is To Crack Your Password, With Kevin MitnickKnowBe4 also offers a Crypto-Ransom guarantee and is confident its training works so well, they will pay your ransom if you get hit with. CryptoDefense Ransomware works by sending spear phishing emails. Learn more about how it works and findransomware removal tips for infected users. Ransomware history, prevention tips, removal, FAQs, information on different strains, current news and KnowBe4's ransomware guarantee.