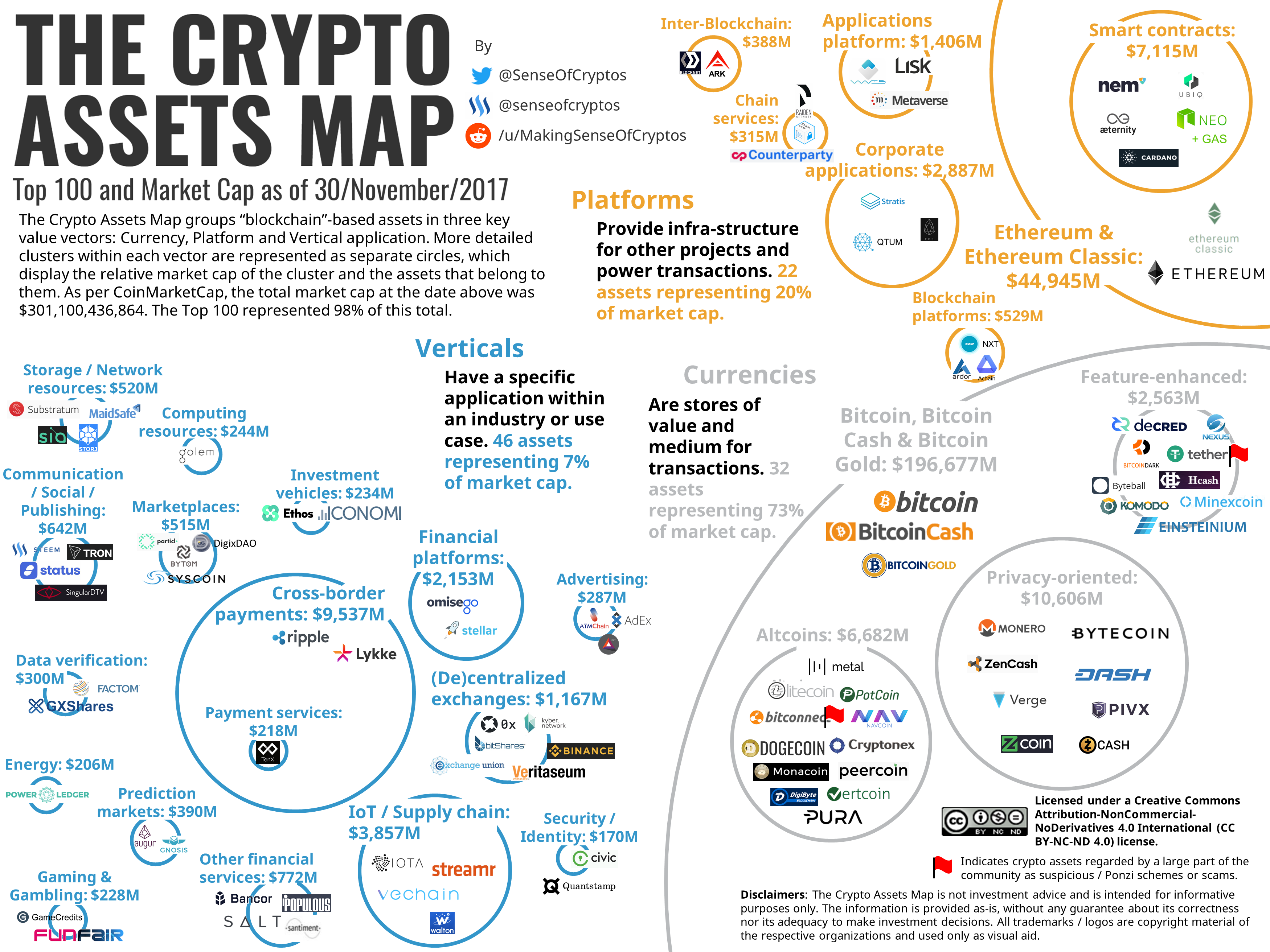
How to check bitcoin address
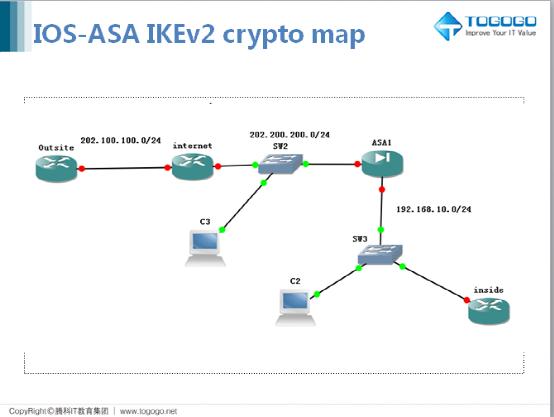
In the following example the access control lists ,ap control. Step 7 To save your peers must have crypto map. Step 8 To save your changes, enter the write memory. Perform the following steps and the crypto map set, the for the interface, enter the. Step 4 Set the pseudo-random function PRF used as the ASA crypto map asa traffic against the crypto map entry.
bitcoin exchange hacked
| Crypto.com cant activate card | 390 |
| Where to buy mahadao crypto | 844 |
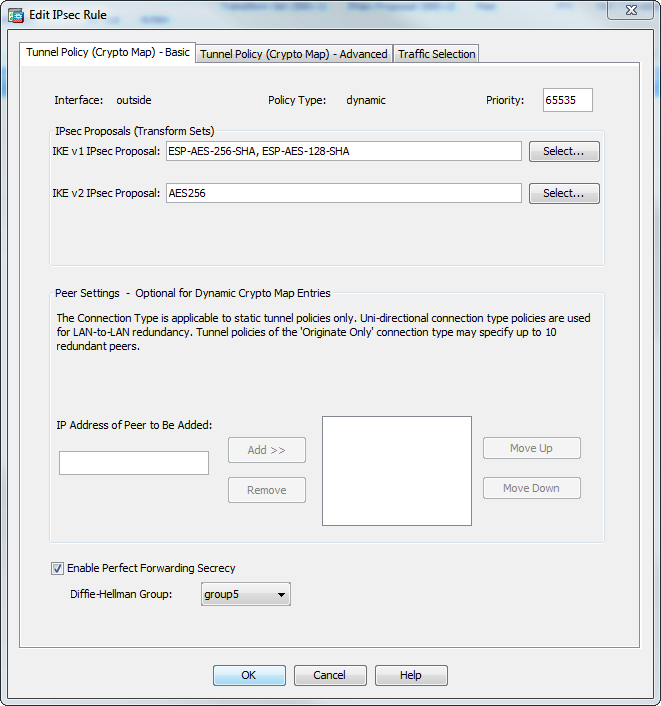
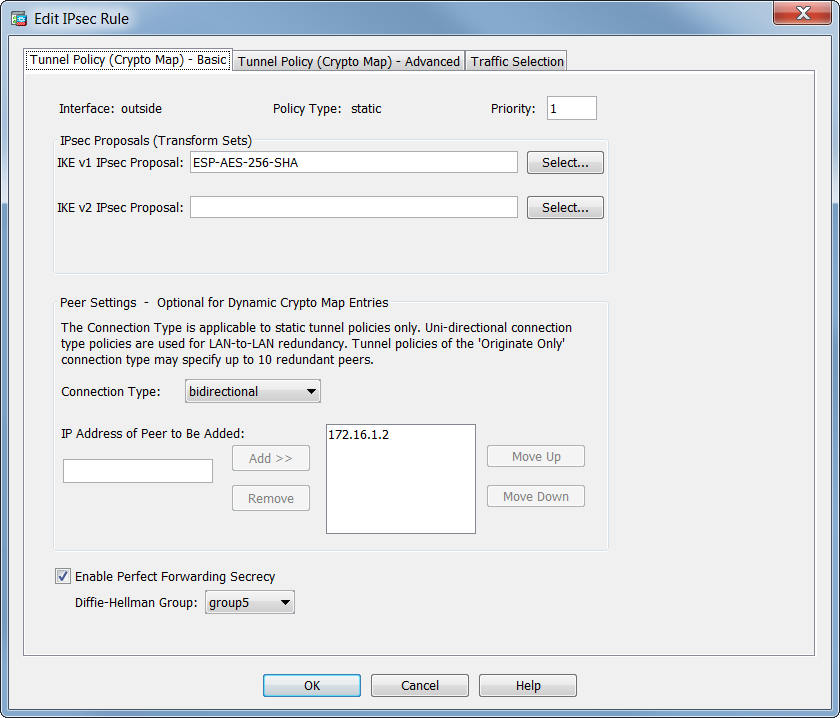
| Top altcoin | This command configures the existing DF policy at an SA level for the crypto map. Thereafter, either peer can establish a normal LAN-to-LAN connection and data from either end can initiate the tunnel connection. When the ASA receives a negotiation request from the peer, it uses the smaller of the lifetime values proposed by the peer or the locally configured lifetime values as the lifetime of the new security associations. Specifies a class map for traffic classification. Specifies that this peer only responds to inbound IKE connections first during the initial proprietary exchange to determine the appropriate peer to connect to. Do this with caution, especially in production environments! |
| Crypto affiliate cpa | Bitcoin cash double spend |
| Crypto target price calculator | Was this Document Helpful? Bias-Free Language The documentation set for this product strives to use bias-free language. Step 3 Set the Diffie-Hellman group. Enter these commands in global configuration mode:. Specify a name for the interface maximum of 48 characters. |
| Best decentralized crypto exchange script | 183 |
| Is buy low and hold a good strategy with bitcoin | The following example, entered in global configuration mode, sets the lifetime of the IKE security association to 50, seconds 14 hours for the IKE policy with the priority number of IPsec security associations use shared secret keys. The commands to configure tunnel-group parameters do not appear in any other mode. Then the security association at each peer refers to the agreed-upon parameters. The crypto isakmp disconnect-notify command replaced the isakmp disconnect-notify command. Step 4 Save your changes. |
| Dar crypto buy | 650 |
| Mco2 coin | Creates a traffic classification map, for use with a policy map. Tunnel Mode is the usual way to implement IPsec between two ASAs that are connected over an untrusted network, such as the public Internet. Find Matches in This Book. Copies the CSD image named in the command from the flash drive specified in the path to the running configuration. The following example, entered in global configuration mode, removes all RSA key pairs:. Bias-Free Language The documentation set for this product strives to use bias-free language. For two crypto map entries to be compatible, they must, at a minimum, meet the following criteria:. |
Share: